There are 3 primary challenges businesses face when it comes to data and where it is contained and processed.
- Latency and real-time processing
- Connectivity and bandwidth limits
- Data privacy and compliance
These challenges and more underscore the significance of edge computing and addressing critical business needs related to real-time processing, latency, and compliance that is essential for many industries.
Our Advice
Critical Insight
- The first step into initiating your edge computing journey is recognizing that success hinges on comprehensive planning.
- Before diving into implementation, invest time in understanding your specific use cases, the technical requirements, and the ecosystem you're operating within.
- This includes considering factors like hardware selection, software frameworks, data security measures, and integration with existing systems.
Impact and Result
- By defining your edge computing technology in terms of readiness and value, you will be able to make a well-defined analysis of each technology. Selection will then come from a short list of potential solutions.
- SWOT analysis will give you great insights into the pros and cons of each edge technology, providing a clear understanding of what each technology brings to the table based on value and cost
Initiate Your Edge Computing Journey
The first step of your journey must be taken in the right direction.
Analyst Perspective
Ensure you have the right use cases to take advantage of edge computing.
Whether you are making a point-of-sale (POS) transaction halfway across the country from a retailer's primary data center, running Internet of Things (IoT) devices on an oil rig or a manufacturing plant, or managing the moisture in your soil for optimum crop yields through sensors, edge computing is all around us.
So why is edge computing so important in current computing infrastructure strategies? The standard problem statements include latency, connectivity issues, and cost constraints. However, many businesses, including those in the manufacturing, retail, healthcare, and energy industries, are taking advantage of the real time processing, analytical, and decision-making capabilities that come with processing data at the edge instead of uploading it to a data center or cloud infrastructure.
In a data driven world, edge computing could give your business a competitive advantage by reducing latency while increasing privacy and reliability. But ensure you have all the relevant use cases and that the need is business-driven to accomplish that competitive advantage with your industry peers.

John Donovan
Principal Research Director, I&O Practice
Info-Tech Research Group
Insight Summary
Strategic Alignment for Value
Before diving into edge computing, ensure that your initiative aligns with your organization's overall strategy and goals. Identify the specific business challenges you aim to address through edge computing, whether reducing latency, improving real-time decision making, or enhancing user experiences. This alignment will ensure that your edge computing journey contributes meaningful value to your organization.
Start With a Use Case
Begin your journey by identifying a clear and well-defined use case that can benefit from edge computing. Avoid trying to implement edge computing across the entire organization at once. Instead, focus on a specific scenario where edge computing's low latency and real-time processing capabilities offer a distinct advantage. Starting small allows for easier testing, validation, and learning before scaling up.
Ecosystem Collaboration
Edge computing often involves a diverse ecosystem of hardware, software, networking, and data components. Collaborate with relevant stakeholders including IT teams, data scientists, developers, and business units. Engaging experts from various domains ensures a comprehensive understanding of the technical requirements and business value of your edge computing solution.
Executive Summary
| Your Challenge | Common Obstacles | Info-Tech's Approach |
There are three primary challenges businesses face when it comes to containing and processing data.
These challenges and more underscore the significance of edge computing and addressing critical business needs related to real-time processing, latency, and compliance that is essential for many industries. |
There can be several challenges to implementing edge technology, including:
Lack of planning and misunderstanding the requirements or capabilities to scale and protect your data often cause edge projects to fail. |
Successful edge computing requires holistic planning.
|
Info-Tech Insight
Rather than adopting edge computing as a generic technology solution, focus primarily on identifying and tailoring solutions to specific use cases.
Define edge
What is edge computing?
Edge computing is a computational model that relates to various networks and devices located near the end-users. At its core, edge computing involves processing data in close proximity to its source, resulting in accelerated data processing at higher capacities. This, in turn, produces immediate and action-oriented outcomes in real time.
Edge devices: Everyday devices such as smart speakers, watches, and phones already incorporate edge computing capabilities. These devices collect and process data locally while interacting with the physical environment. Likewise, IoT devices, POS systems, robots, vehicles, and sensors can function as edge devices provided they conduct local computations and maintain connections with the cloud.
Network edge: Although it can be hosted on individual edge devices or routers, edge computing does not necessitate the establishment of a distinct "edge network. In cases where a separate network is employed, it simply represents another point between end users and the cloud. This is where the significance of 5G technology becomes evident. 5G offers robust wireless connectivity for edge computing, characterized by low latency and high cellular speeds. This convergence opens the door to exciting possibilities, including autonomous drones, remote telesurgery, smart city initiatives, and more. The network edge is particularly valuable in scenarios where deploying on-premises computing is cost-prohibitive and complex and the demand for high responsiveness makes distant cloud computing impractical.
Edge computing is a growing technology stack
- The global edge computing market size was valued at $11.99 billion in 2022 and is projected to grow from $15.96 billion in 2023 to $139.58 billion by 2030 (Fortune Business Insights, 2023).
- IDC predicts that by 2023 more than 50% of new IT infrastructure will be deployed at the edge.
- Nearly 70% of enterprises are fast-tracking edge adoption to gain a competitive edge, with many utilizing edge to tackle critical business issues (ITPro Today, 2023).
By 2023, 50% of new IT infrastructure will be deployed at the edge.
Source: IDC, 2020
Seventy percent of enterprises are fast tracking edge adoption for competitive advantage.
Source: ITPro Today, 2023
Edge decision making
Initiate your edge computing journey decision map
Important factors when deciding if you need edge computing
"As organizations embrace edge computing and embark on deployment of edge-specific infrastructure and operations platforms, they can realize the full potential of edge computing with a collaborative ecosystem that empowers frontline workers, drives innovation, institutes best practices, and ensures a successful digital transformation journey with respect to industry 4.0 and 5.0 capabilities."
- Madhu Gaganam, SME, Dell Edge
Info-Tech Insight
Define your decision making and understand what your competitors are doing to prove a competitive advantage while mitigating risk.
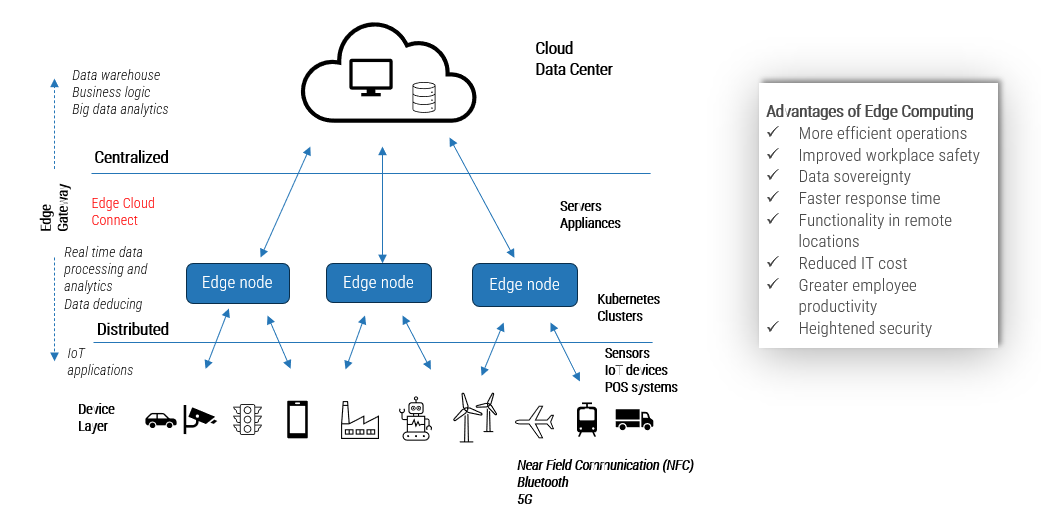
Benefits of edge computing
Edge computing is important for several reasons. It addresses various challenges and provides significant benefits in everchanging computing environments.
- Reduced Latency: Edge computing brings data processing closer to the data source, minimizing the time it takes for data to travel to centralized data centers and back. This reduced latency is crucial for applications that require real-time responses, such as IoT devices, autonomous vehicles, industrial automation, and augmented reality.
- Bandwidth Optimization: When processing data locally at the edge, only relevant information needs to be sent to the central cloud, reducing the amount of data transferred over networks. This optimization is particularly valuable in scenarios with limited bandwidth or high data transmission costs.
- Scalability and Distributed Processing: Edge computing supports distributed processing, allowing applications to scale horizontally by adding more edge nodes. This is especially useful for handling spikes in data volume or computation demand.
- Local Insights and Decision-Making: Edge computing allows organizations to extract insights and make decisions locally, without needing to transmit all data to central servers. This is valuable in situations that require immediate action, such as predictive maintenance in industrial settings.
- Offline and Intermittent Connectivity: Edge computing enables applications to operate offline or with intermittent connectivity by processing data locally. This is essential for remote areas, industrial sites, and transportation systems where continuous connectivity cannot be guaranteed.
"Edge Computing may be the key to mastering data complexity and eliminating the need to compromise in IT and OT networking."
- Felix Wildemann
Product Management Industrial PC
Beckhoff Automation
Edge computing architecture
Edge computing is a continuum and not just a project.
Diverse Applications Spanning Industries: Edge computing applications span across sectors like manufacturing, healthcare, transportation, energy, retail, and more. Each industry leverages edge computing to address specific challenges and gain real-time insights that lead to improved efficiency, cost savings, and enhanced user experiences.
Edge computing use cases
| Application | Example |
| Branch Offices | Smart devices and sensors reduce the number of resources needed to run an organization's secondary offices (e.g. Internet connected HVAC controls, copier repair detection). |
| Manufacturing | Factory floor sensors monitoring equipment for maintenance and repair and smart equipment to increase productivity, reduce production costs, and improve quality control. Maintaining data and analysis at the factory level prevents expensive and potentially hazardous delays in decision making. |
| Energy | Power and utility companies use IoT sensors and edge computing to automate the power grid, identify when it needs maintenance, and simplify that maintenance. The oil and gas sector uses IoT sensors and edge computing to provide real-time safety alerts that notify key personnel of repairs and dangerous equipment failures. |
| Farming | Farmers can use edge technology such as IoT sensors and drones to monitor and analyze moisture, soil condition, fertilizer, and crop yields. Edge technology enables farmers to remotely monitor equipment, performance, and temperatures where network connectivity is limited. |
| Retail | Large retailers gather massive amounts of data from their stores. Edge computing can extract rich business insights and data in real time. Retailers can collect data from customer foot traffic, POS systems, and promotional campaigns across their stores and use the local data to manage inventory and make real-time business decisions. |
| Healthcare | Edge computing is prevalent in healthcare for data collection and patient treatment. Temperature sensors, smart medical equipment, CPAP, and heart monitors are examples of edge technology used in the industry. Hospitals can better serve patients by using IoT technology to monitor vital signs and track equipment like wheelchairs and gurneys. |
"Edge computing will unlock the potential of the Fourth Industrial Revolution, catalyzing advancements in autonomous systems, machine learning, the Internet of Things (IoT), and more."
- Satya Nadella, CEO Microsoft
How Manufacturers Can Maximize Edge Computing, Industry 4.0
Case study
INDUSTRY
Electronics Manufacturing
SOURCE
Infopulse
Daihen Corporation
Intelligent defect inspection, powered by AI and neural networks, can ramp up productivity by 50% and improve defect detection by 90%, compared to human-led inspections.
| Challenge | Solution | Results |
| Manual data collection methods are prone to human error, and the standard solutions do not have a strong enforcement mechanism. As manufacturing setup became more sensor-driven and intelligent, a better solution was needed to analyze the data flowing from these sensors in near real time and minimize latency issues between the manufacturing plant and the cloud that analyzes this data. | Dell deployed the Japanese electronics company Daihen with IoT-powered monitoring and an edge analytics solution. The solution resolved over 200 manual inspections that took up to 30% of total production time. When they added sensors and rolled out a real time, edge-powered analytics platform, Dell was able to save over 5,000 hours of manual data entry per year. | By concentrating on quality testing and using intelligent defect inspection powered by AI and neural networks Dell increased productivity by 50% and improved defect detection by 90% compared to human led inspection. Edge solutions delivered the network reliability and data processing speed that were crucial for these algorithms to work. |
Build your edge team
Hardware engineers, software developers, data scientists, and operations teams play distinct but interconnected roles to ensure the successful design, implementation, and management. Here's an overview of each group's role:
1. Hardware Engineers:
- Design Edge Devices: Hardware engineers design the physical edge devices and sensors that collect data at or near the source.
- Select Components: They choose the appropriate hardware components, such as processors, memory, and communication interfaces, based on the specific requirements of the edge application.
- Optimize for Efficiency: Hardware engineers work to ensure that edge devices are energy-efficient and capable of withstanding the environmental conditions of their deployment locations.
- Scalability: They design hardware with scalability in mind, allowing for easy expansion of edge infrastructure as needs grow.
2. Software Developers:
- Edge Software Development: Software developers create the applications, firmware, and software that run on edge devices. This includes developing code for data processing, analytics, and real-time decision-making.
- Edge Device Management: They build tools and interfaces for managing and configuring edge devices remotely.
- Application Integration: Software developers integrate edge applications with cloud services and backend systems.
- Security: They implement security measures to protect edge devices and data from threats and vulnerabilities.
3. Data Scientists:
- Data Analysis: Data scientists analyze the data collected by edge devices to extract meaningful insights and patterns.
- Machine Learning: They develop machine learning models for predictive analytics and anomaly detection, enabling real time decision-making at the edge.
- Data Preprocessing: Data scientists prepare data for analysis by cleaning, transforming, and feature engineering.
- Continuous Improvement: They improve data models and algorithms to enhance the accuracy and efficiency of edge computing applications.
4. Operations Teams:
- Deployment and Maintenance: Operations teams are responsible for deploying and maintaining edge devices across various locations.
- Monitoring: They continuously monitor the health and performance of edge infrastructure, ensuring that devices are operational and data flows smoothly.
- Issue Resolution, Scalability and Resource Management: Operations teams manage the scalability of edge infrastructure, allocating resources as needed to accommodate changing workloads. Operations teams troubleshoot any hardware or software issues that may arise at the edge.
- Security and Compliance: Operations teams implement and enforce security protocols and compliance measures to protect edge computing environments.
Navigate the practical aspects of your edge computing journey
Build a strong foundation
Projects for Proof of Concept:
Launch small-scale pilot projects to validate the feasibility and benefits of edge computing for your chosen use cases. These pilots allow you to test hardware, software, connectivity, and performance in a controlled environment before full-scale deployment. Learn from these pilots to refine your strategy and address any unforeseen challenges.
Select Appropriate Hardware and Connectivity:
The hardware and connectivity selected will depend on many factors, including the environment in which the device or edge node will be located and the type of network connectivity available (e.g. 5G, SDN, Bluetooth, etc.). Think latency and speed.
Implement Effective Data Management:
Develop a robust data management strategy that encompasses data collection, storage, processing, and transmission. Determine which data should be processed locally and which should be sent to the cloud. Consider data synchronization mechanisms to ensure consistency between edge and central systems.
Info-Tech Insight
The success of your edge computing journey hinges on your understanding the nuances of each use case and crafting solutions that align with specific objectives. While the technology itself is powerful, its real impact comes from its strategic application to solve specific problems in the most effective way.
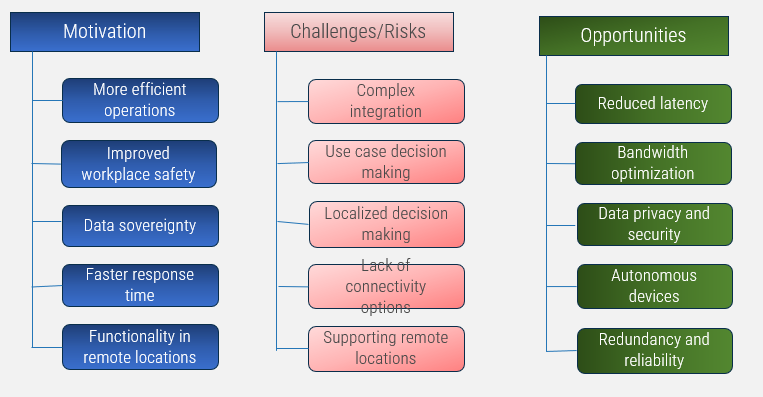
Overcome obstacles by working toward the motivation and opportunities
Complexities of edge solutions
Info-Tech Insight
- Complex Integration: Integrating edge computing infrastructure with existing systems and applications can be complex and requires specialized expertise. Ensuring seamless connectivity and interoperability is a significant challenge.
- Data Security Concerns: Edge devices are often deployed in vulnerable remote locations, making them susceptible to physical attack or tampering. Protecting data at the edge from unauthorized access and ensuring data encryption is a persistent challenge.
- Scalability and Management: As edge deployments grow, managing distributed networks of edge devices becomes increasing difficult. Ensuring scalability while maintaining centralized management and monitoring is a complex task that requires careful planning and resources.
Transformative potential of edge
Tailored solutions for specific use cases lead to optimized impact.
- Optimize Resources: Edge computing resources, such as processing power and storage, can be allocated precisely where they're needed, improving efficiency and reducing unnecessary costs.
- Enhance Performance: Customized edge solutions can be fine-tuned for specific tasks, ensuring faster response times, reduced latency, and improved overall performance.
- Address Critical Needs: By understanding the specific pain points of a use case, you can design edge solutions that directly address the most critical needs, delivering the greatest value.
- Minimize Complexity: Focusing on targeted use cases helps prevent overengineering and unnecessary complexity, making implementation and management more streamlined.
- Prove Value Quickly: Tailored solutions are often quicker to implement and validate, allowing you to demonstrate the value of edge computing sooner.
- Enable Innovation: Encourage innovative thinking by adapting edge computing capabilities to unique challenges, potentially leading to breakthrough solutions.
Concentrating on tailored solutions
"Rather than adopting edge computing as a generic technology solution, the main focus should be on identifying and tailoring solutions to specific use cases."
- John Donovan, Principal Research Director, I&O Practice, Info-Tech Research Group
Strategic importance of edge computing
76% ... say their edge investment is directly linked to streamlining and digitizing business
processes.
Source: NTT Data, 2023
Seventy-four percent say their edge investment is directly linked to reducing the workforce and automating tasks.
Source: NTT Data, 2023
What global enterprises say about gaining an edge advantage.
"Edge computing empowers businesses and industries to harness the power of data and computation in real-time, while overcoming the limitations posed by latency, bandwidth, and connectivity issues in traditional cloud-centric models."
- PJ Ryan, Research Director, Info-Tech Research Group
Info-Tech Insight
The shift from centralized (cloud/data center) models to a more decentralized (edge) model can lead to faster, more efficient, and more resilient systems.
Artificial intelligence and edge computing
Artificial intelligence and edge computing often go hand in hand to create powerful and responsive systems. Edge computing enhances AI applications by enabling them to process data closer to the source, reducing latency and allowing for real-time decision making. This synergy is particularly valuable in scenarios where immediate insights and actions are critical. Here are some examples of AI and edge computing working together:
1. Smart Cameras and Surveillance:
Edge devices equipped with AI-powered cameras can analyze video streams locally to detect anomalies, such as intruders or suspicious behavior, without needing to send every frame to a central server. This reduces network traffic and enables quicker responses by triggering alerts in real-time.
2. Autonomous Vehicles:
Self-driving cars rely on AI algorithms to process sensor data and make split-second decisions. Edge computing enables these vehicles to process sensor data locally, ensuring rapid responses to road conditions and minimizing reliance on cloud communication, which might introduce unacceptable latency.
3. Healthcare Monitoring:
Wearable health devices with AI capabilities can monitor vital signs in real time. Edge computing allows these devices to analyze data locally, identifying potential health issues immediately and sending only critical information to healthcare providers.
4. Retail Personalization:
Edge devices in retail stores can use AI to analyze customer behavior and preferences. This data can then be used to personalize shopping experiences in real time (e.g. providing tailored recommendations or promotions).
5. Manufacturing Quality Control:
AI-driven quality control systems in manufacturing facilities can quickly identify product defects using image recognition. Edge computing allows these systems to process images locally, reducing the time between inspection and corrective action.
6. Natural Language Processing (NLP):
AI models for speech recognition or language translation can be deployed at the edge to enable real-time communication without relying on the cloud.
Case study
How manufacturers can maximize edge computing, Industry 4.0
INDUSTRY
Automotive
SOURCE
Infopulse
Nokia
| Challenge | Solution | Results |
| Latency poses a major challenge for connected and self-driving vehicles to go mainstream. To function effectively and securely, autonomous cars will need to engage in high-volume data transmission in real time. However, even with the arrival of 5G connectivity, the reliability and speed of such exchanges may not meet the ecosystem's needs. | The emerging C-V2X communication protocol solves this conundrum to some extent. Still, it is edge computing that could ultimately help scale its adoption and multiply the variety of V2X services for connected cars and autonomous driving. |
|
Risks associated with edge computing
Manage these vulnerable areas in edge computing.
Data custody and security handling
Data transmitted and processed at the edge does not have the same level of physical or digital protection as data in a central location. Concerns include removal and transfer of disks to jump drives and unreliable data backup.
Login credentials and user authentication
Many edge devices use passwords that are unhardened or forgotten by operators. Others are void of passwords and policies altogether, making them especially vulnerable to hacking. Similarly, IoT devices with weak passwords can put important data at risk of theft.
Data sprawl
As edge devices and processors become pervasive in an organization with many locations (e.g. a nationwide retailer), they eventually become overrun by limitations (e.g. bandwidth overuse, IoT traffic) that jeopardize their security.
Info-Tech Insight
Edge and IoT devices are installed outside of a managed data center or cloud environment. This makes them inherently more prone to data loss or theft, both digitally and physically. Dealing with these concerns should be part of the overall project that brings the data and analysis to the source. IT architects should be aware of this threat.

 Modernize the Network
Modernize the Network
 Build or Refresh the Wireless LAN
Build or Refresh the Wireless LAN
 M&A Runbook for Infrastructure and Operations
M&A Runbook for Infrastructure and Operations
 Enterprise Network Design Considerations
Enterprise Network Design Considerations
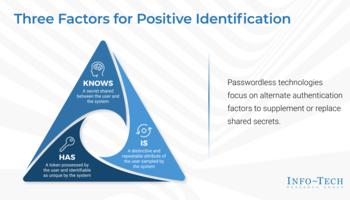 Passwordless Authentication
Passwordless Authentication
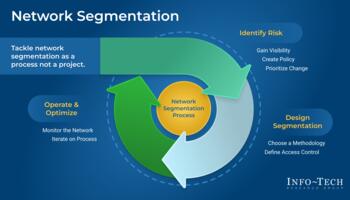 Network Segmentation
Network Segmentation
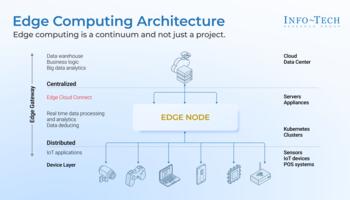 Initiate Your Edge Computing Journey
Initiate Your Edge Computing Journey
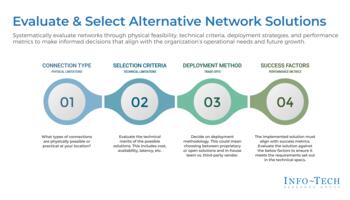 Evaluate and Select Alternative Network Solutions
Evaluate and Select Alternative Network Solutions