Unlock Improve Security Governance With a Security Steering Committee
Get Instant Access
Improve Security Governance With a Security Steering Committee
Build an inclusive committee to enable holistic strategic decision making.
- Security is still seen as an IT problem rather than a business risk, resulting in security governance being relegated to the existing IT steering committee.
- Security is also often positioned in the organization where they are not privy to the details of the organization’s overall strategy. Security leaders struggle to get the full enterprise picture.
Our Advice
Critical Insight
- Work to separate the Information Security Steering Committee (ISSC) from the IT Steering Committee (ITSC). Security transcends the boundaries of IT and needs an independent, eclectic approach to make strategic decisions.
- Be the lawyer, not the cop. Ground your communications in business terminology to facilitate a solution that makes sense to the entire organization.
- Develop and stick to the agenda. Continued engagement from business stakeholders requires sticking to a strategic level-focused agenda. Dilution of purpose will lead to dilution in attendance.
Impact and Result
- Define a clear scope of purpose and responsibilities for the ISSC to gain buy-in and consensus for security governance receiving independent agenda time from the broader IT organization.
- Model the information flows necessary to provide the steering committee with the intelligence to make strategic decisions for the enterprise.
- Determine membership and responsibilities that shift with the evolving security landscape to ensure participation reflects interested parties and that money being spent on security mitigates risk across the enterprise.
- Create clear presentation material and strategically oriented meeting agendas to drive continued participation from business stakeholders and executive management.
Improve Security Governance With a Security Steering Committee Research & Tools
Start here – read the Executive Brief
Read our concise Executive Brief to find out how to improve your security governance with a security steering committee, review Info-Tech’s methodology, and understand the ways we can support you in completing this project.
1. Define committee purpose and responsibilities
Identify the purpose of your committee, determine the capabilities of the committee, and define roles and responsibilities.
2. Determine information flows, membership & accountabilities
Determine how information will flow and the process behind that.
3. Operate the Information Security Steering Committee
Define your meeting agendas and the procedures to support those meetings. Hold your kick-off meeting. Identify metrics to measure the committee’s success.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
10.0/10
Overall Impact
$10,000
Average $ Saved
20
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Testimonial
The Regional Municipality of Durham
Guided Implementation
10/10
$10,000
20
Alabama Department of Corrections
Guided Implementation
9/10
N/A
N/A
The best parts of our experience was gaining Logan's insight on the functions of an Information Security Charter and how it sets up the organizatio... Read More
The best parts of our experience was gaining Logan's insight on the functions of an Information Security Charter and how it sets up the organizational framework of governance for the security program. Logan's review of our charter document was also very helpful in identifying potential areas of confusion as it was written, which guided the conversation on what we were trying to accomplish and how to better simplify the objectives. Thanks to Logan for a great experience and as always, thanks to InfoTech for such a great service. Read Less
Clark County, WA
Guided Implementation
8/10
$12,733
10
Aaron was very knowledgeable and a pleasure to speak with
Pact Group PTY Ltd
Guided Implementation
10/10
N/A
18
Toronto District School Board
Guided Implementation
7/10
N/A
N/A
Improve Security Governance With a Security Steering Committee
Build an inclusive committee to enable holistic strategic decision making.
ANALYST PERSPECTIVE
"Having your security organization’s steering committee subsumed under the IT steering committee is an anachronistic framework for today’s security challenges. Conflicts in perspective and interest prevent holistic solutions from being reached while the two permanently share a center stage.
At the end of the day, security is about existential risks to the business, not just information technology risk. This focus requires its own set of business considerations, information requirements, and delegated authorities. Without an objective and independent security governance body, organizations are doomed to miss the enterprise-wide nature of their security problems."
– Daniel Black, Research Manager, Security Practice, Info-Tech Research GroupOur understanding of the problem
This Research Is Designed For:
- CIOs
- CISOs
- IT/Security Leaders
This Research Will Help You:
- Develop an effective information security steering committee (ISSC) that ensures the right people are involved in critical decision making.
- Ensure that business and IT strategic direction are incorporated into security decisions.
This Research Will Also Assist:
- Information Security Steering Committee (ISSC) members
This Research Will Help Them:
- Formalize roles and responsibilities.
- Define effective security metrics.
- Develop a communication plan to engage executive management in the organization’s security planning.
Executive summary
Situation
- Successful information security governance requires a venue to address security concerns with participation from across the entire business.
- Without access to requisite details of the organization – where we are going, what we are trying to do, how the business expects to use its technology – security can not govern its strategic direction.
Complication
- Security is still seen as an IT problem rather than a business risk, resulting in security governance being relegated to the existing IT steering committee.
- Security is also often positioned in the organization where they are not privy to the details of the organization’s overall strategy. Security leaders struggle to get the full enterprise picture.
Resolution
- Define a clear scope of purpose and responsibilities for the Information Security Steering Committee to gain buy-in and consensus for security governance receiving independent agenda time from the broader IT organization.
- Model the information flows necessary to provide the steering committee with the intelligence to make strategic decisions for the enterprise.
- Determine membership and responsibilities that shift with the evolving security landscape to ensure participation reflects interested parties and that money being spent on security mitigates risk across the enterprise.
- Create security metrics that are aligned with committee members’ operational goals to incentivize participation.
- Create clear presentation material and strategically oriented meeting agendas to drive continued participation from business stakeholders and executive management.
Info-Tech Insight
- Work to separate the ISSC from the IT Steering Committee (ITSC). Security transcends the boundaries of IT and needs an independent, eclectic approach to make strategic decisions.
- Be the lawyer, not the cop. Ground your communications in business terminology to facilitate a solution that make sense to the entire organization.
- Develop and stick to the agenda. Continued engagement from business stakeholders requires sticking to a strategic level-focused agenda. Dilution of purpose will lead to dilution in attendance.
Empower your security team to act strategically with an ISSC
Establishing an Information Security Steering Committee (ISSC)
Even though security is a vital consideration of any IT governance program, information security has increasingly become an important component of the business, moving beyond the boundaries of just the IT department.
This requires security to have its own form of steering, beyond the existing IT Steering Committee, that ensures continual alignment of the organization’s security strategy with both IT and business strategy.
An ISSC should have three primary objectives:
- Direct Strategic Planning The ISSC formalizes organizational commitments to strategic planning, bringing visibility to key issues and facilitating the integration of security controls that align with IT and business strategy.
- Institute Clear Accountability The ISSC facilitates the involvement and commitment of executive management through clearly defined roles and accountabilities for security decisions, ensuring consistency in participation as the organization’s strategies evolve.
- Optimize Security Resourcing The ISSC maximizes security by monitoring the implementation of the security strategic plan, making recommendations on prioritization of effort, and securing necessary resources through the planning and budgeting processes, as necessary.
What does the typical ISSC do?
Ensuring proper governance over your security program is a complex task that requires ongoing care and feeding from executive management to succeed.
Your ISSC should aim to provide the following core governance functions for your security program:
- Define Clarity of Intent and Direction How does the organization’s security strategy support the attainment of the business and IT strategies? The ISSC should clearly define and communicate strategic linkage and provide direction for aligning security initiatives with desired outcomes.
- Establish Clear Lines of Authority Security programs contain many important elements that need to be coordinated. There needs to be clear and unambiguous authority, accountability, and responsibility defined for each element so lines of reporting/escalation are clear and conflicting objectives can be mediated.
- Provide Unbiased Oversight The ISSC should vet the organization’s systematic monitoring processes to make certain there is adherence to defined risk tolerance levels and ensure that monitoring is appropriately independent from the personnel responsible for implementing and managing the security program.
- Optimize Security Value Delivery Optimized value delivery occurs when strategic objectives for security are achieved and the organization’s acceptable risk posture is attained at the lowest possible cost. This requires constant attention to ensure controls are commensurate with any changes in risk level or appetite.
Formalize the most important governance functions for your organization
Creation of an ISSC is deemed the most important governance and oversight practice that a CISO can implement, based on polling of IT security leaders analyzing the evolving role of the CISO.
Relatedly, other key governance practices reported – status updates, upstream communications, and executive-level sponsorship – are within the scope of what organizations traditionally formalize when establishing their ISSC.
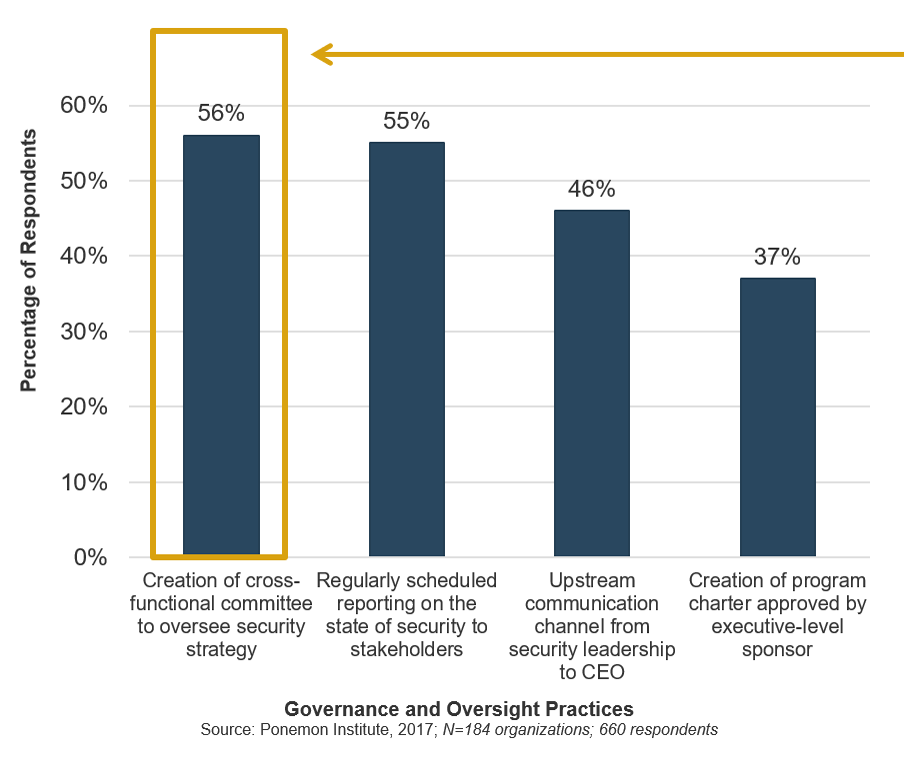
Despite the clear benefits of an ISSC, organizations are still falling short
83% of organizations have not established formal steering committees to evaluate the business impact and risks associated with security decisions. (Source: 2017 State of Cybersecurity Metrics Report)
70% of organizations have delegated cybersecurity oversight to other existing committees, providing security limited agenda time. (Source: PwC 2017 Annual Corporate Director Survey)
"This is a group of risk managers an institution would bring together to deal with a response anyway. Having them in place to do preventive discussions and formulate policy to mitigate the liability sets and understand compliance obligations is just powerful." (Kirk Bailey, CISO, University of Washington)
Prevent the missteps that make 9 out of 10 steering committees unsuccessful
Why Do Steering Committees Fail?
- A lack of appetite for a steering committee from business partners. An effective ISSC requires participation from core members of the organization’s leadership team. The challenge is that most business partners don’t understand the benefits of an ISSC and the responsibilities aren’t tailored to participants’ needs or interests. It’s the CISO’s (or senior IT/security leader’s) responsibility to make this case to stakeholders and right-size the committee responsibilities and membership.
- ISSC committees are given inappropriate responsibilities. The steering committee is fundamentally about decision making; it’s not a working committee. Security leadership typically struggles with clarifying these responsibilities on two fronts: either the responsibilities are too vague and there is no clear way to execute on them within a meeting or responsibilities are too tactical and require knowledge that participants do not have. Responsibilities should determine who is on the ISSC, not the other way around.
- Lack of process around execution. An ISSC is only valuable if members are able to successfully execute on its mandate. Without well-defined processes it becomes nearly impossible for the ISSC to be actionable. As a result, participants lack the information they need to make critical decisions, agendas are unmet, and meetings are seen as a waste of time.
Use these icons to help direct you as you navigate this research
Use these icons to help guide you through each step of the blueprint and direct you to content related to the recommended activities.

This icon denotes a slide where a supporting Info-Tech tool or template will help you perform the activity or step associated with the slide. Refer to the supporting tool or template to get the best results and proceed to the next step of the project.

This icon denotes a slide with an associated activity. The activity can be performed either as part of your project or with the support of Info-Tech team members, who will come onsite to facilitate a workshop for your organization.
Info-Tech offers various levels of support to best suit your needs
DIY Toolkit |
Guided Implementation |
Workshop |
Consulting |
| "Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful." | "Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track." | "We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place." | "Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project." |
Diagnostics and consistent frameworks used throughout all four options
Improve Security Governance With a Security Steering Committee – project overview
1. Define Committee Purpose and Responsibilities |
2. Determine Information Flows, Membership & Accountabilities |
3. Operate the Information Security Steering Committee |
|
 Best-Practice Toolkit |
1.1 Tailor Info-Tech’s Information Security Steering Committee Charter Template to define terms of reference for the ISSC 1.2 Conduct a SWOT analysis of your information security governance capabilities 1.3 Identify the responsibilities and duties of the ISSC 1.4 Draft the committee purpose statement of your ISSC |
2.1 Define your SIPOC model for each of the ISSC responsibilities 2.2 Identify committee participants and responsibility cadence 2.3 Define ISSC participant RACI for each of the responsibilities |
3.1 Define the ISSC meeting agendas and procedures 3.2 Define which metrics you will report to the ISSC 3.3 Hold a kick-off meeting with your ISSC members to explain the process, responsibilities, and goals 3.4 Tailor the Information Security Steering Committee Stakeholder Presentation template 3.5 Present the information to the security leadership team 3.6 Schedule your first meeting of the ISSC |
Guided Implementations |
|
|
|
 Onsite Workshop |
This blueprint can be combined with other content for onsite engagements, but is not a standalone workshop. | ||
Phase 1 Outcome:
|
Phase 2 Outcome:
|
Phase 3 Outcome:
|
Improve Security Governance With a Security Steering Committee
PHASE 1
Define Committee Purpose and Responsibilities
Phase 1: Define Committee Purpose and Responsibilities
ACTIVITIES:
- 1.1 Tailor Info-Tech’s Information Security Steering Committee Charter Template to define terms of reference for the ISSC
- 1.2 Conduct a SWOT analysis of your information security governance capabilities
- 1.3 Identify the responsibilities and duties of the ISSC
- 1.4 Draft the committee purpose statement for your ISSC
OUTCOMES:
- Conduct an analysis of your current information security governance capabilities and identify opportunities and weaknesses.
- Define a clear scope of purpose and responsibilities for your ISSC.
- Begin to customize your ISSC charter.
Info-Tech Insight
Balance vision with direction. Purpose and responsibilities should be defined so that they encompass your mission and objectives to the enterprise in clear terms, but provide enough detail that you can translate the charter into operational plans for the security team.
Tailor Info-Tech’s Information Security Steering Committee Charter Template to define terms of reference for the ISSC
A charter is the organizational mandate that outlines the purpose, scope, and authority of the ISSC. Without a charter, the steering committee’s value, scope, and success criteria are unclear to participants, resulting in unrealistic stakeholder expectations and poor organizational acceptance.
Start by reviewing Info-Tech’s template. Throughout the next two sections we will help you to tailor its contents.
- Committee Purpose: The rationale, benefits of, and overall function of the committee.
- Organization and Membership: Who is on the committee and how is participation measured against organizational need.
- Responsibilities and Duties: What tasks/decisions the accountable committee is making.
- RACI: Who is accountable, responsible, consulted, and informed regarding each responsibility.
- Committee Procedures and Agendas: Includes how the committee will be organized and how the committee will interact and communicate with interested parties.
Download the Information Security Steering Committee Charter to customize your organization’s charter
Conduct a SWOT analysis of your information security governance capabilities
INPUT: Survey outcomes, Governance overview handouts
OUTPUT: SWOT analysis, Top identified challenges and opportunities
- Hold a meeting with your IT leadership team to conduct a SWOT analysis on your current information security governance capabilities.
- In small groups, or individually, have each group complete a SWOT analysis for one of the governance areas. For each consider:
- Strengths: What is currently working well in this area?
- Weaknesses: What could you improve? What are some of the challenges you’re experiencing?
- Opportunities: What are some organizational trends that you can leverage? Consider whether your strengths or weaknesses could create opportunities.
- Threats: What are some key obstacles across people, process, and technology?
- Have each team or individual rotate until each person has contributed to each SWOT. Add comments from the stakeholder survey to the SWOT.
- As a group, rank the inputs from each group and highlight the top five challenges and the top five opportunities you see for improvement.
Identify the responsibilities and duties of the ISSC
INPUT: SWOT analysis, Survey reports
OUTPUT: Defined ISSC responsibilities
- With your security leadership team, review the typical responsibilities of the ISSC on the following slides (also included in the templated text of the charter linked below).
- Print off the following two slides, and in small teams or individually, identify which responsibilities the ISSC should have in your organization, brainstorm any additional responsibilities, and document reasoning.
- Have each team present to the larger group, track the similarities and differences between each of the groups, and come to consensus on the list of categories and responsibilities.
- Complete a sanity check: review your SWOT analysis. Do the responsibilities you’ve identified resolve the critical challenges or weaknesses?
- As a group, consider the responsibilities and whether you can reasonably implement those in one year or if there are any that will need to wait until year two of the committee.
Add or modify responsibilities in Info-Tech’s Information Security Steering Committee Charter.
Typical ISSC responsibilities and duties
Use the following list of responsibilities to customize the list of responsibilities your ISSC may take on. These should link directly to the Responsibilities and Duties section of your ISSC charter.
Strategic Oversight
- Provide oversight and ensure alignment between information security strategy and company objectives.
- Assess the adequacy of resources and funding to sustain and advance successful security programs and practices for identifying, assessing, and mitigating cybersecurity risks across all business functions.
- Review controls to prevent, detect, and respond to cyber-attacks or information or data breaches involving company electronic information, intellectual property, data, or connected devices.
- Review the company’s cyberinsurance policies to ensure appropriate coverage.
- Provide recommendations, based on security best practices, for significant technology investments.
Policy Governance
- Review company policies pertaining to information security and cyberthreats, taking into account the potential for external threats, internal threats, and threats arising from transactions with trusted third parties and vendors.
- Review privacy and information security policies and standards and the ramifications of updates to policies and standards.
- Establish standards and procedures for escalating significant security incidents to the ISSC, board, other steering committees, government agencies, and law enforcement, as appropriate.
Typical ISSC responsibilities and duties (continued)
Use the following list of responsibilities to customize the list of responsibilities your ISSC may take on. These should link directly to the Responsibilities and Duties section of your ISSC charter.
Risk Governance
- Review and approve the company’s information risk governance structure and key risk management processes and capabilities.
- Assess the company’s high-risk information assets and coordinate planning to address information privacy and security needs.
- Provide input to executive management regarding the enterprise’s information risk appetite and tolerance.
- Review the company’s cyber-response preparedness, incident response plans, and disaster recovery capabilities as applicable to the organization’s information security strategy.
- Promote an open discussion regarding information risk and integrate information risk management into the enterprise’s objectives.
Monitoring & Reporting
- Receive periodic reports and coordinate with management on the metrics used to measure, monitor, and manage cyber and IT risks posed to the company and to review periodic reports on selected risk topics as the Committee deems appropriate.
- Review reports provided by the IT organization regarding the status of and plans for the security of the company’s data stored on internal resources and with third-party providers.
- Monitor and evaluate the quality and effectiveness of the company’s technology security, capabilities for disaster recovery, data protection, cyberthreat detection and cyber incident response, and management of technology-related compliance risks.
Review the organization’s security strategy to solidify understanding of the ISSC’s purpose
The ISSC should consistently evolve to reflect the strategic purpose of the security program. If you completed Info-Tech’s Security Strategy methodology, review the results to inform the scope of your committee. If you have not completed Info-Tech’s methodology, determining these details should be achieved through iterative stakeholder consultations.
Strategy Components |
ISSC Considerations |
Security Pressure Analysis |
Review the ten security domains and your organization’s pressure levels to review the requisite maturity level of your security program. Consider how this may impact the focus of your ISSC. |
Security Drivers/Obligations |
Review how your security program supports the attainment of the organization’s business objectives. By what means should the ISSC support these objectives? This should inform the rationale, benefits, and overall function of the committee. |
Security Strategy Scope and Boundaries |
Consider the scope and boundaries of your security program to reflect on what the program is responsible for securing. Is this reflected adequately in the language of the committee’s purpose? Should components be added or redacted? |
Draft the committee purpose statement of your ISSC
INPUT: SWOT Analysis, Security Strategy
OUTPUT: ISSC Committee Purpose
- In a meeting with your IT leadership team – and considering the organization’s security strategy, defined responsibilities, and opportunities and threats identified – review the example goal statement in the Information Security Steering Committee Charter, and identify whether any of these statements apply to your organization. Select the statements that apply and collaboratively make any changes needed.
- Define unique goal statements by considering the following questions:
- What three things would you realistically list for the ISSC to achieve?
- If you were to accomplish three things in the next year, what would those be?
- With those goal statements in mind, consider the overall purpose of the committee. The purpose statement should be a reflection of what the committee does, why, and the goals.
- Have each individual review the example purpose statement and draft what they think a good purpose statement would be.
- Present each statement, and work together to determine a best-of-breed statement.
Alter the Committee Purpose section in the Information Security Steering Committee Charter.

About Info-Tech
Info-Tech Research Group is the world’s fastest-growing information technology research and advisory company, proudly serving over 30,000 IT professionals.
We produce unbiased and highly relevant research to help CIOs and IT leaders make strategic, timely, and well-informed decisions. We partner closely with IT teams to provide everything they need, from actionable tools to analyst guidance, ensuring they deliver measurable results for their organizations.
MEMBER RATING
10.0/10
Overall Impact
$10,000
Average $ Saved
20
Average Days Saved
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve.
What Is a Blueprint?
A blueprint is designed to be a roadmap, containing a methodology and the tools and templates you need to solve your IT problems.
Each blueprint can be accompanied by a Guided Implementation that provides you access to our world-class analysts to help you get through the project.
Need Extra Help?
Speak With An Analyst
Get the help you need in this 3-phase advisory process. You'll receive 7 touchpoints with our researchers, all included in your membership.
Guided Implementation 1: Define committee purpose and responsibilities
- Call 1: Identify the responsibilities and duties of the ISSC.
- Call 2: Draft the committee purpose of the ISSC.
Guided Implementation 2: Determine information flows, membership & accountabilities
- Call 1: Determine SIPOC modeling of information flows.
- Call 2: Determine accountabilities and responsibilities.
Guided Implementation 3: Operate the Information Security Steering Committee
- Call 1: Set operational standards.
- Call 2: Determine effectiveness metrics.
- Call 3: Understand steering committee best practices.
Author
Daniel Black
Related Content: Governance, Risk & Compliance
Unlock Improve Security Governance With a Security Steering Committee
Get Instant Access
This content is exclusive to members.
Get instant access by signing up!
Search Code: 87043
Last Revised: November 23, 2018
TAGS:
Security steering committee, information security steering committee, cybersecurity steering committee, information security governance steering committee, cybersecurity governance, information security governance, security governance and management, security metrics, information security metrics, cybersecurity metrics, CISO, security program, information security program, cybersecurity program, information security strategy, information security roadmap, security roadmap, LFBP Assess Your Cybersecurity Insurance Policy
Assess Your Cybersecurity Insurance Policy
 Achieve Digital Resilience by Managing Digital Risk
Achieve Digital Resilience by Managing Digital Risk
 Combine Security Risk Management Components Into One Program
Combine Security Risk Management Components Into One Program
 Prevent Data Loss Across Cloud and Hybrid Environments
Prevent Data Loss Across Cloud and Hybrid Environments
 Build an IT Risk Management Program
Build an IT Risk Management Program
 Close the InfoSec Skills Gap: Develop a Technical Skills Sourcing Plan
Close the InfoSec Skills Gap: Develop a Technical Skills Sourcing Plan
 Develop and Deploy Security Policies
Develop and Deploy Security Policies
 Fast Track Your GDPR Compliance Efforts
Fast Track Your GDPR Compliance Efforts
 Build a Security Compliance Program
Build a Security Compliance Program
 Embed Privacy and Security Culture Within Your Organization
Embed Privacy and Security Culture Within Your Organization
 Establish Effective Security Governance & Management
Establish Effective Security Governance & Management
 Improve Security Governance With a Security Steering Committee
Improve Security Governance With a Security Steering Committee
 Develop Necessary Documentation for GDPR Compliance
Develop Necessary Documentation for GDPR Compliance
 Reduce and Manage Your Organization’s Insider Threat Risk
Reduce and Manage Your Organization’s Insider Threat Risk
 Satisfy Customer Requirements for Information Security
Satisfy Customer Requirements for Information Security
 Responsibly Resume IT Operations in the Office
Responsibly Resume IT Operations in the Office
 Master M&A Cybersecurity Due Diligence
Master M&A Cybersecurity Due Diligence
 Integrate IT Risk Into Enterprise Risk
Integrate IT Risk Into Enterprise Risk
 Present Security to Executive Stakeholders
Present Security to Executive Stakeholders
 Deliver Customer Value by Building Digital Trust
Deliver Customer Value by Building Digital Trust
 Address Security and Privacy Risks for Generative AI
Address Security and Privacy Risks for Generative AI
 Protect Your Organization's Online Reputation
Protect Your Organization's Online Reputation