- Most organizations do not have a clear understanding of their current security posture, their security goals, and the specific security services they require. Without a clear understanding of their needs, organizations may struggle to identify a partner that can meet their requirements.
- Breakdowns and lack of communication can be a significant obstacle, especially when clear lines of communication with partners, including regular check-ins, reporting, and incident response protocols, have not been clearly established.
- Ensuring that security partners’ systems and processes integrate seamlessly with existing systems can be a challenge for most organizations in addition to making sure that security partners have the necessary access and permissions to perform their services effectively.
- Adhering to security policies is rarely a priority to users as compliance often feels like an interference to daily workflow. For a lot of organizations, security policies are not having the desired effect.
Our Advice
Critical Insight
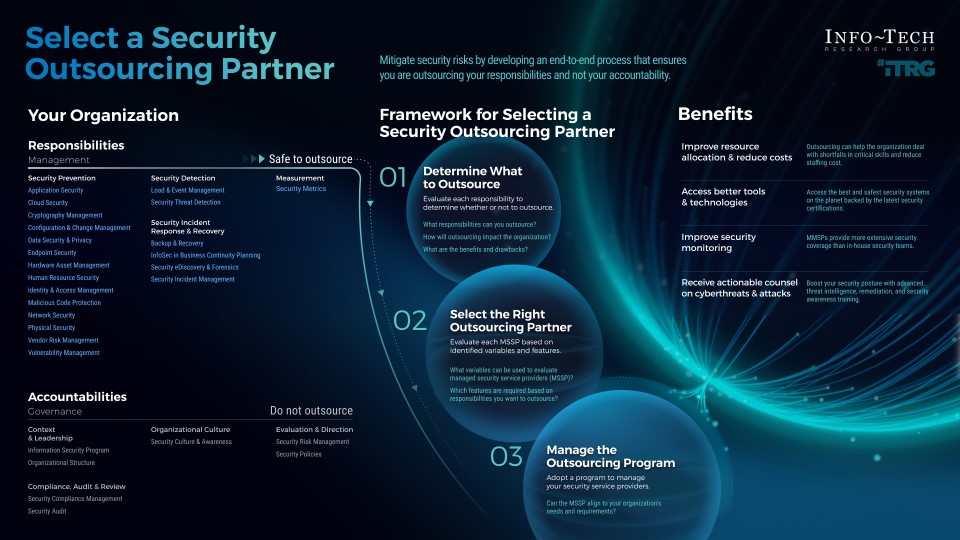
- You can outsource your responsibilities but not your accountability.
- Be aware that in most cases, the traditional approach is more profitable to MSSPs, and they may push you toward one, so make sure you get the service you want, not what they prescribe.
Impact and Result
- Determine which security responsibilities can be outsourced and which should be insourced and the right procedure to outsourcing to gain cost savings, improve resource allocation, and boost your overall security posture.
Member Testimonials
After each Info-Tech experience, we ask our members to quantify the real-time savings, monetary impact, and project improvements our research helped them achieve. See our top member experiences for this blueprint and what our clients have to say.
8.3/10
Overall Impact
$13,739
Average $ Saved
8
Average Days Saved
Client
Experience
Impact
$ Saved
Days Saved
Waymo
Guided Implementation
10/10
N/A
N/A
Learning
Medcan
Guided Implementation
8/10
$25,000
10
Kevin was measured and thoughtful in his recommendations for us to move forward with the context of being a small business and relevant services.
City Of Fort Collins
Guided Implementation
7/10
$2,479
5
Kevin was willing to meet even tho CoFC is early in its journey toward a cybersecurity strategy and roadmap.
Mueller, Inc.
Guided Implementation
10/10
N/A
N/A
Garfield County IT
Guided Implementation
9/10
$12,776
10
The Info Tech tools will be helpful. I have no negative comments.
Christchurch City Council, NZ
Guided Implementation
9/10
N/A
5
Jerry's Foods
Guided Implementation
10/10
$31,833
20
we are still not done so not sure why the survey yet.


 Build Your Security Operations Program From the Ground Up
Build Your Security Operations Program From the Ground Up
 Develop a Security Operations Strategy
Develop a Security Operations Strategy
 Develop and Deploy Security Policies
Develop and Deploy Security Policies
 Establish an Effective System of Internal IT Controls to Mitigate Risks
Establish an Effective System of Internal IT Controls to Mitigate Risks
 Select a Security Outsourcing Partner
Select a Security Outsourcing Partner
 Embed Security Into the DevOps Pipeline
Embed Security Into the DevOps Pipeline
 Reinforce End-User Security Awareness During Your COVID-19 Response
Reinforce End-User Security Awareness During Your COVID-19 Response
 Cybersecurity Priorities in Times of Pandemic
Cybersecurity Priorities in Times of Pandemic
 Build a Security Metrics Program to Drive Maturity
Build a Security Metrics Program to Drive Maturity
 Build a Service-Based Security Resourcing Plan
Build a Service-Based Security Resourcing Plan
 Secure IT/OT Convergence
Secure IT/OT Convergence
 Integrate Physical Security and Information Security
Integrate Physical Security and Information Security
 Prepare for Post-Quantum Cryptography
Prepare for Post-Quantum Cryptography
 Build an Automation Roadmap to Streamline Security Processes
Build an Automation Roadmap to Streamline Security Processes