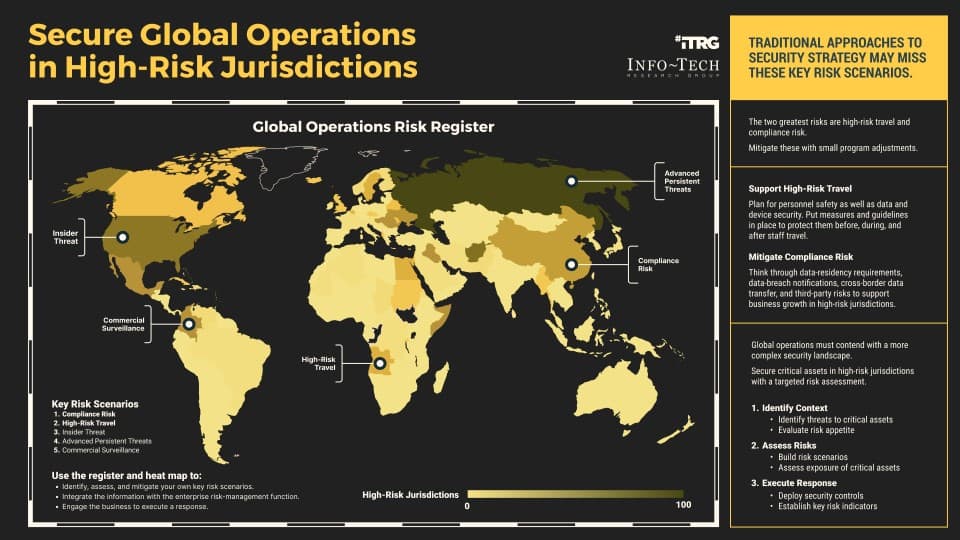
Business operations in high-risk areas of the world contend with complex threat environments and risk scenarios that often require a unique response. But traditional approaches to security strategy often miss these jurisdictional risks, leaving organizations vulnerable to threats that range from cybercrime and data breaches to fines and penalties.
Security leaders need to identify high-risk jurisdictions, inventory critical assets, identify vulnerabilities, assess risks, and identify security controls necessary to mitigate those risks.
Secure operations and protect critical assets in high-risk regions
Across risks that include insider threats and commercial surveillance, the two greatest vulnerabilities that organizations face in high-risk parts of the world are travel and compliance. Organizations can make small adjustments to their security program to address these risks:
- Support high-risk travel: Put measures and guidelines in place to protect personnel, data, and devices before, during, and after employee travel.
- Mitigate compliance risk: Consider data residency requirements, data breach notification, cross-border data transfer, and third-party risks to support business growth.
Using these two prevalent risk scenarios in high-risk jurisdictions as examples, this research walks you through the steps to analyze the threat landscape, assess security risks, and execute a response to mitigate them.
Workshop: Secure Operations in High-Risk Jurisdictions
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
Module 1: Identify Context for Risk Assessment
The Purpose
Assess business requirements and evaluate security pressures to set the context for the security risk assessment.
Key Benefits Achieved
- Understand the goals of the organization in high-risk jurisdictions.
- Assess the threats to critical assets in these jurisdictions and capture stakeholder expectations for information security.
Activities
Outputs
Determine assessment scope.
Determine business goals.
Determine compliance obligations.
Determine risk appetite.
- Business requirements
Conduct pressure analysis.
- Security pressure analysis
Module 2: Analyze Key Risk Scenarios for High-Risk Jurisdictions
The Purpose
Build key risk scenarios for high-risk jurisdictions.
Key Benefits Achieved
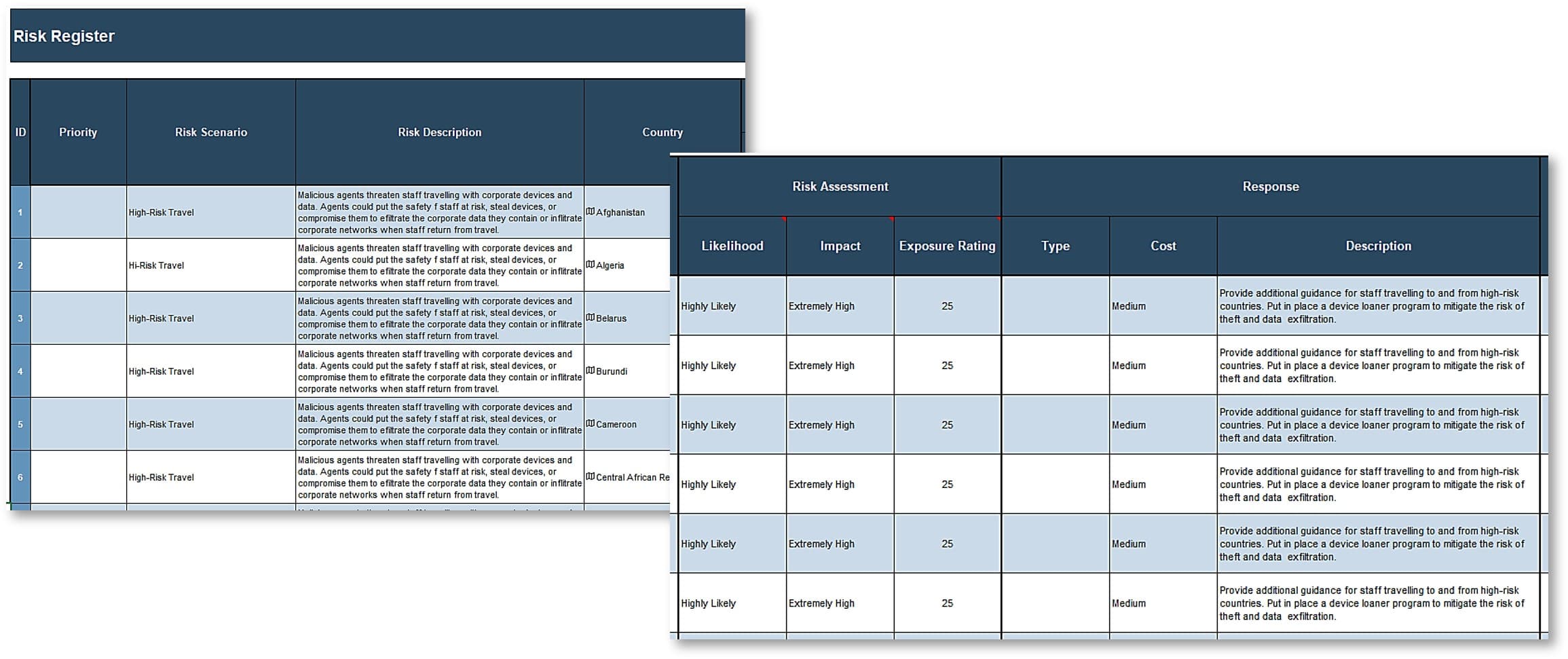
- Identify critical assets in high-risk jurisdictions, their vulnerabilities to relevant threats, and the adverse impact should malicious agents exploit them.
- Assess risk exposure of critical assets in high-risk jurisdictions.
Activities
Outputs
Identify critical assets.
Identify threats.
Assess risk likelihood.
Assess risk impact.
- Key risk scenarios
- Jurisdictional risk exposure
- Jurisdictional Risk Register and Heat Map
Module 3: Build Risk Treatment Roadmap
The Purpose
Prioritize and treat jurisdictional risks to critical assets.
Key Benefits Achieved
- Build an initiative roadmap to reduce residual risks in high-risk jurisdictions.
Activities
Outputs
Identify and assess risk response.
Assess residual risks.
Identify security controls.
Build initiative roadmap.
- Action plan to mitigate key risk scenarios



_preview3848.jpg?1693949745) Design and Implement a Business-Aligned Security Program
Design and Implement a Business-Aligned Security Program
_-_16x9_-_hires_previewb049.png?1710356443) Build an Information Security Strategy
Build an Information Security Strategy
 Secure Operations in High-Risk Jurisdictions
Secure Operations in High-Risk Jurisdictions
 Develop a Security Awareness and Training Program That Empowers End Users
Develop a Security Awareness and Training Program That Empowers End Users
 Build, Optimize, and Present a Risk-Based Security Budget
Build, Optimize, and Present a Risk-Based Security Budget
 Hire or Develop a World-Class CISO
Hire or Develop a World-Class CISO
 Fast Track Your GDPR Compliance Efforts
Fast Track Your GDPR Compliance Efforts
 Build a Cloud Security Strategy
Build a Cloud Security Strategy
 Identify the Components of Your Cloud Security Architecture
Identify the Components of Your Cloud Security Architecture
 Security Priorities 2022
Security Priorities 2022
 2020 Security Priorities Report
2020 Security Priorities Report
 Manage Third-Party Service Security Outsourcing
Manage Third-Party Service Security Outsourcing
 Select a Security Outsourcing Partner
Select a Security Outsourcing Partner
 Improve Security Governance With a Security Steering Committee
Improve Security Governance With a Security Steering Committee
 The First 100 Days as CISO
The First 100 Days as CISO
 Determine Your Zero Trust Readiness
Determine Your Zero Trust Readiness
 Cost-Optimize Your Security Budget
Cost-Optimize Your Security Budget
 Threat Preparedness Using MITRE ATT&CK®
Threat Preparedness Using MITRE ATT&CK®
 Build a Zero Trust Roadmap
Build a Zero Trust Roadmap
 Security Priorities 2023
Security Priorities 2023
 Security Priorities 2024
Security Priorities 2024